MD2 generator
Created on 3 October, 2025 • Generator tools • 76 views • 2 minutes read
Learn about the MD2 generator, its history, working process, and uses. Discover why MD2 is outdated and what modern hashing algorithms to use instead.
MD2 Generator: Everything You Need to KnowIn the world of cryptography, hash functions play an important role in ensuring data integrity and verification. One such algorithm is MD2 (Message Digest Algorithm 2), which was widely used in the early days of secure computing. Although it has been replaced by stronger algorithms today, the MD2 generator still carries relevance for educational, compatibility, and legacy system purposes.
What is MD2?
MD2 is a cryptographic hash function developed by Ronald Rivest in 1989. It produces a 128-bit hash value from any input data, such as text or files. The algorithm was designed for older systems and was once a popular choice for data validation and digital signatures.
However, due to advances in cryptanalysis, MD2 is now considered obsolete and insecure for modern applications. Despite this, it remains useful in understanding the evolution of hashing technology.
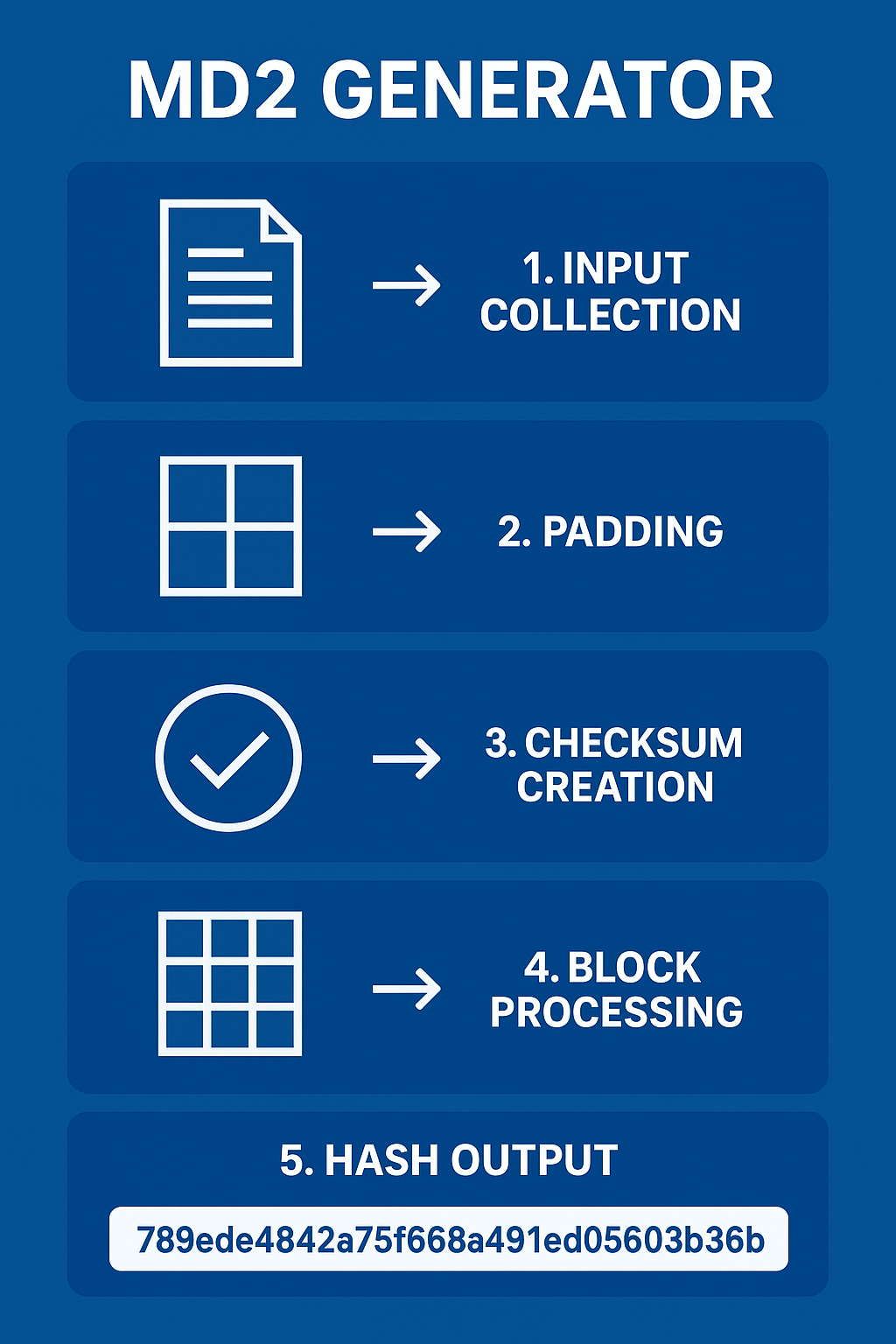
How an MD2 Generator Works
An MD2 generator is a tool that converts input data into a fixed hash output. The process can be explained in a few simple steps:
Input Collection – The generator takes any string or file as input.
Padding – The input is padded so its length is divisible by 16 bytes.
Checksum Creation – A 16-byte checksum is added to strengthen integrity checks.
Block Processing – The input is divided into blocks and processed with transformation rules.
Final Hash Output – The result is a 128-bit hash (commonly displayed as a 32-character hexadecimal string).
A key feature of MD2 is that even the smallest change in input produces a completely different hash output, making it useful for data integrity verification.
Applications of MD2 Generators
Even though MD2 is no longer suitable for strong cryptographic protection, it is still found in specific use cases:
Legacy Systems – Some older applications and protocols continue to depend on MD2.
Digital Signatures – Early public key cryptography standards included MD2 for message authentication.
File Verification – It can be used for basic data integrity checks.
Education and Research – Students and professionals study MD2 to understand early cryptographic designs.
MD2 vs Modern Hash Functions
Algorithm Output Size Security Level Usage Today
MD2 128-bit Insecure Legacy tools
MD5 128-bit Weak File checksums
SHA-1 160-bit Weak Old certificates
SHA-256 256-bit Strong Security, blockchain
SHA-3 224–512-bit Strongest Advanced encryption
As the table shows, MD2 has been outpaced by modern algorithms like SHA-256 and SHA-3, which are used in blockchain, encryption, and digital security.
Conclusion
The MD2 generator is a historical cryptographic tool that produces a 128-bit hash value from input data. While it once played a crucial role in data integrity and authentication, it is now considered insecure for modern applications. Its primary relevance lies in legacy system support, backward compatibility, and educational study.
For secure hashing in today’s world, stronger algorithms such as SHA-256, SHA-3, or bcrypt are highly recommended. However, understanding MD2 remains essential for anyone studying the evolution of cryptography.
Popular posts
-
Barcode readerMisc Tools • 160 views
-
Color pickerMisc Tools • 122 views
-
Exif readerMisc Tools • 117 views
-
SHA-256 generatorGenerator tools • 93 views
-
Ip LookupChecker Tools • 90 views