SHA-256 generator
Created on 5 October, 2025 • Generator tools • 100 views • 2 minutes read
Generate secure 256-bit hashes instantly with a free SHA-256 generator. Protect passwords, verify data integrity, and enhance online security with SHA-256 encryption.
SHA-256 Generator – Secure Your Data with Advanced Hash EncryptionWhat is a SHA-256 Generator?
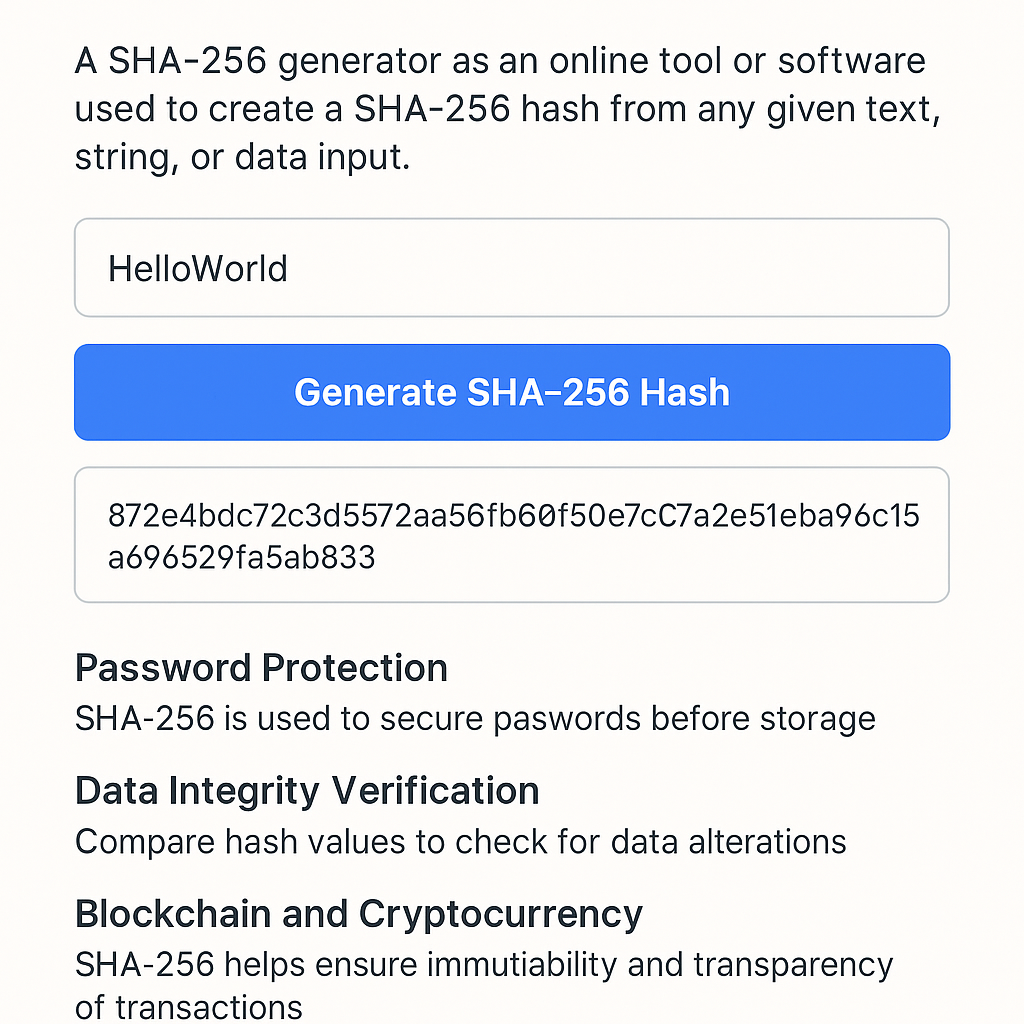
A SHA-256 generator is an online tool or software used to create a SHA-256 hash from any given text, string, or data input. SHA-256 stands for Secure Hash Algorithm 256-bit, a cryptographic function that converts input data into a unique 64-character hexadecimal string. It is a one-way function, meaning once data is converted into SHA-256 hash, it cannot be reversed or decrypted back to its original form.
SHA-256 is part of the SHA-2 (Secure Hash Algorithm 2) family, developed by the National Security Agency (NSA) and widely used in data encryption, password security, blockchain technology, and digital signatures.
How Does a SHA-256 Generator Work?
A SHA-256 generator applies a complex mathematical algorithm to your input data. This algorithm processes your text and produces a fixed-length 256-bit (32-byte) hash value, regardless of the size of the original input.
For example:
Input: HelloWorld
Output: 872e4bdc72c3d5... (64-character hash)
The key properties of SHA-256 include:
Deterministic Output – The same input always produces the same hash.
Irreversibility – You cannot decode or revert a hash to its original form.
Uniqueness – Even a small change in input generates a completely different hash.
Security – It is computationally infeasible to find two inputs with the same hash (collision resistance).
Why Use a SHA-256 Generator?
1. Password Protection
SHA-256 is commonly used to secure passwords before storing them in databases. Instead of saving plain text passwords, developers hash them with SHA-256 to prevent unauthorized access.
2. Data Integrity Verification
By comparing hash values before and after data transfer, you can confirm that files have not been altered or corrupted. This ensures data integrity in file sharing, software distribution, and cloud storage.
3. Blockchain and Cryptocurrency
SHA-256 plays a critical role in blockchain technology. For example, Bitcoin uses SHA-256 to ensure the immutability and transparency of transactions.
4. Digital Signatures and Certificates
SHA-256 is used in SSL/TLS certificates to create secure connections between browsers and web servers. It validates the authenticity of websites and encrypted communication.
Features of an Online SHA-256 Generator
Instant Hash Conversion: Generate SHA-256 hash in seconds.
Supports Any Text Input: Convert any text, password, or file data.
Copy and Share Easily: One-click copy function for convenience.
Free and Secure: No data storage or tracking—complete privacy.
Cross-Platform: Works on desktop, mobile, and browsers.
How to Use a SHA-256 Generator Online
Go to a trusted SHA-256 generator website.
Enter or paste your text into the input box.
Click the “Generate SHA-256 Hash” button.
Instantly receive the 64-character hash output.
Copy or download the hash for verification or storage.
Conclusion
A SHA-256 generator is an essential tool for anyone dealing with data security, web development, or blockchain verification. It provides a simple yet powerful way to safeguard information through cryptographic hashing. Whether you’re securing passwords, validating files, or ensuring blockchain integrity, SHA-256 remains one of the most trusted and widely adopted encryption algorithms in the digital world.
Popular posts
-
Barcode readerMisc Tools • 160 views
-
Color pickerMisc Tools • 122 views
-
Exif readerMisc Tools • 117 views
-
SHA-256 generatorGenerator tools • 93 views
-
Ip LookupChecker Tools • 90 views