SHA-3/224 generator
Created on 5 October, 2025 • Generator tools • 70 views • 2 minutes read
Generate secure 224-bit hashes using the SHA-3/224 generator. Learn how this modern cryptographic tool ensures data integrity, password protection, and blockchain security.
SHA-3/224 Generator – Secure Hash Function for Modern CryptographyIntroduction to SHA-3/224 Generator
The SHA-3/224 generator is a cryptographic tool that produces a 224-bit (28-byte) hash value from any input data using the SHA-3 (Secure Hash Algorithm 3) standard. Developed by the National Institute of Standards and Technology (NIST), SHA-3 is the latest member of the SHA family, built on the Keccak algorithm. Unlike previous SHA-2 algorithms, SHA-3 is based on a different internal structure (sponge construction), providing enhanced resistance against known cryptographic attacks.
A SHA-3/224 hash generator ensures secure, one-way hashing, meaning once a hash is created, it cannot be reversed to reveal the original input. This makes it ideal for applications like password hashing, digital signatures, blockchain technology, and data integrity verification.
How the SHA-3/224 Generator Works
A SHA-3/224 generator converts any text or file input into a fixed-length, 224-bit hash output. The process follows these key steps:
Input Processing: The input data (string, file, or message) is taken by the algorithm.
Sponge Function Application: The data is absorbed into a large internal state using a bitwise permutation function and a padding rule.
Compression and Squeezing: The algorithm “squeezes” the state to produce a fixed-length output of 224 bits.
Output Hash: The result is a unique, irreversible hash value representing the input data.
This unique approach ensures that even a minor change in input — for example, changing a single character — completely alters the resulting hash output.
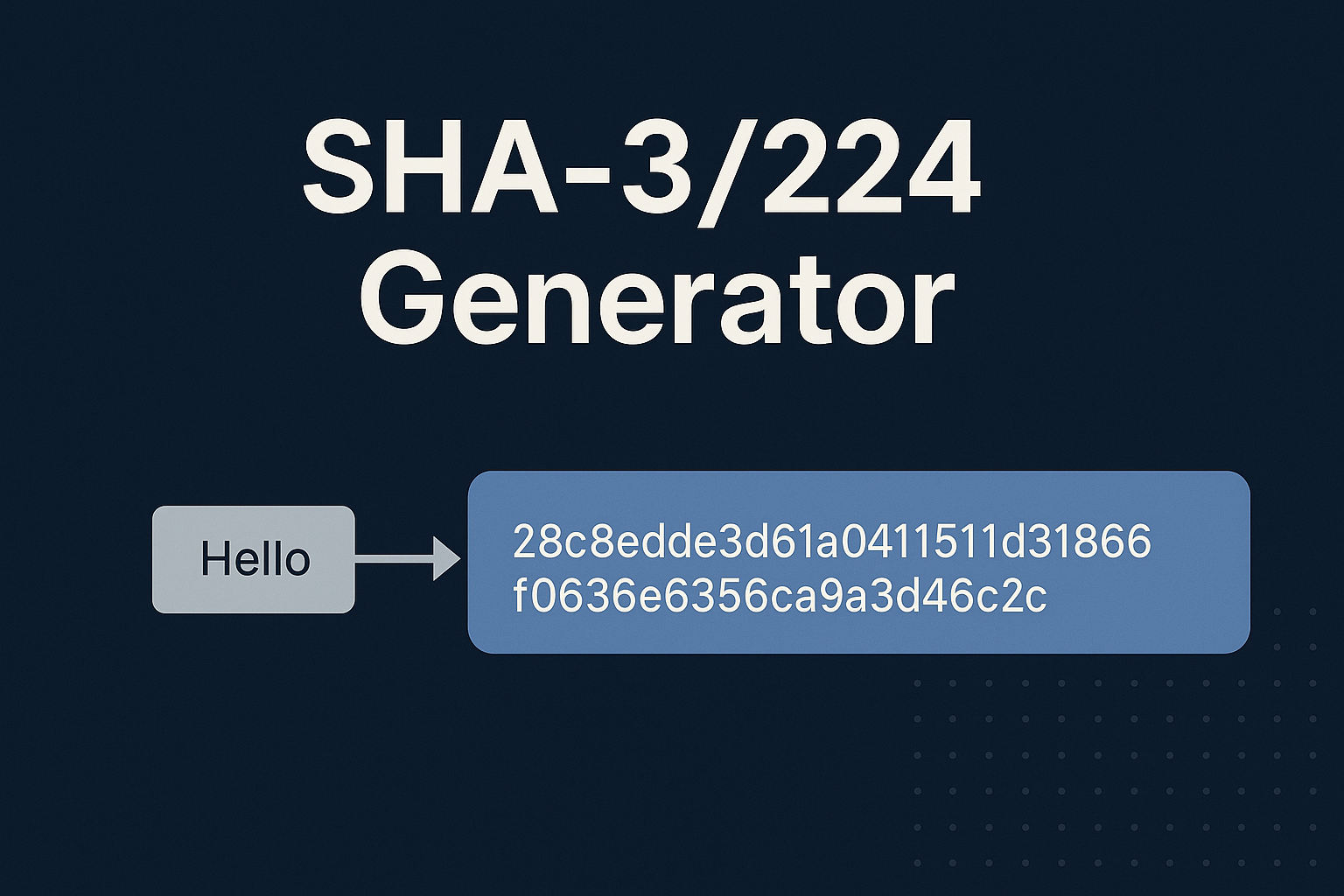
Example:
Input: Hello
SHA3-224 Hash: 28c8edde3d61a0411511d3b1866f0636e6356ca9a3d46c2c
Features and Benefits of SHA-3/224 Generator
1. High Security and Collision Resistance
SHA-3/224 offers robust protection against collision attacks, where two different inputs produce the same hash. It’s designed with quantum resistance in mind, providing security for the future of digital communication.
2. Better Than SHA-2
While SHA-2 remains secure, SHA-3/224 introduces a completely different internal structure, making it immune to certain theoretical weaknesses that could affect SHA-2 algorithms.
3. Fast and Efficient
Modern implementations of SHA-3/224 are optimized for performance, allowing fast hash generation even for large data sets.
4. Ideal for Blockchain and Authentication
SHA-3/224 is widely used in blockchain validation, message authentication codes (MACs), and digital signatures, ensuring data integrity across distributed systems.
Applications of SHA-3/224 Generator
Password Hashing: Securely stores passwords using unique hash values.
Blockchain Systems: Ensures block data is immutable and tamper-proof.
File Verification: Validates data integrity during uploads, downloads, or transfers.
Cryptographic Signatures: Confirms authenticity and prevents forgery.
API and Data Security: Protects API keys, tokens, and sensitive information.
Conclusion
The SHA-3/224 generator represents the next evolution of cryptographic hashing. With its strong security foundation, efficient performance, and modern design, it provides a reliable method for safeguarding digital data. Whether you’re a developer, security engineer, or blockchain enthusiast, using SHA-3/224 ensures your applications are built on a future-proof cryptographic standard.
Popular posts
-
Barcode readerMisc Tools • 160 views
-
Color pickerMisc Tools • 122 views
-
Exif readerMisc Tools • 117 views
-
SHA-256 generatorGenerator tools • 93 views
-
Ip LookupChecker Tools • 90 views